If you use conditional grants in SAS® Visual Analytics for row level security, then you might be interested in one of the enhancements available in our recent Metacoda Plug-ins 5.0 release. This new release adds support for automated metadata security testing of the permission conditions behind conditional grants. Conditional grants, sometimes known as row-level permissions or row-level security, allow you to grant limited access to a subset of data based on an expression. If someone is in a constrained group then they only get to see the rows where the expression evaluates to true.
If you’re using conditional grants to restrict certain groups of users to specific subsets of data then you’d probably be keenly interested in making sure those conditional grants remain in place. You wouldn’t want to discover at some future time that, due to unexpected changes in the permission conditions, those groups of users have been getting much broader access to data than should have been allowed.
We’ve enhanced Metacoda Plug-ins in version 5 to help people maintain the integrity of their permission conditions in the following areas:
- The Protected Object Reviewer can now generate metadata security test XML files containing tests for any permission conditions found in metadata (which includes conditional grants applied to any VA tables).
- The Metadata Security Testing Framework will run any tests for permission conditions (including VA conditional grants) that it finds in a metadata security test XML file. These tests can be run interactively via the Test Runner plug-in, or in batch for automated regular testing with email alerts when any test failures are detected.
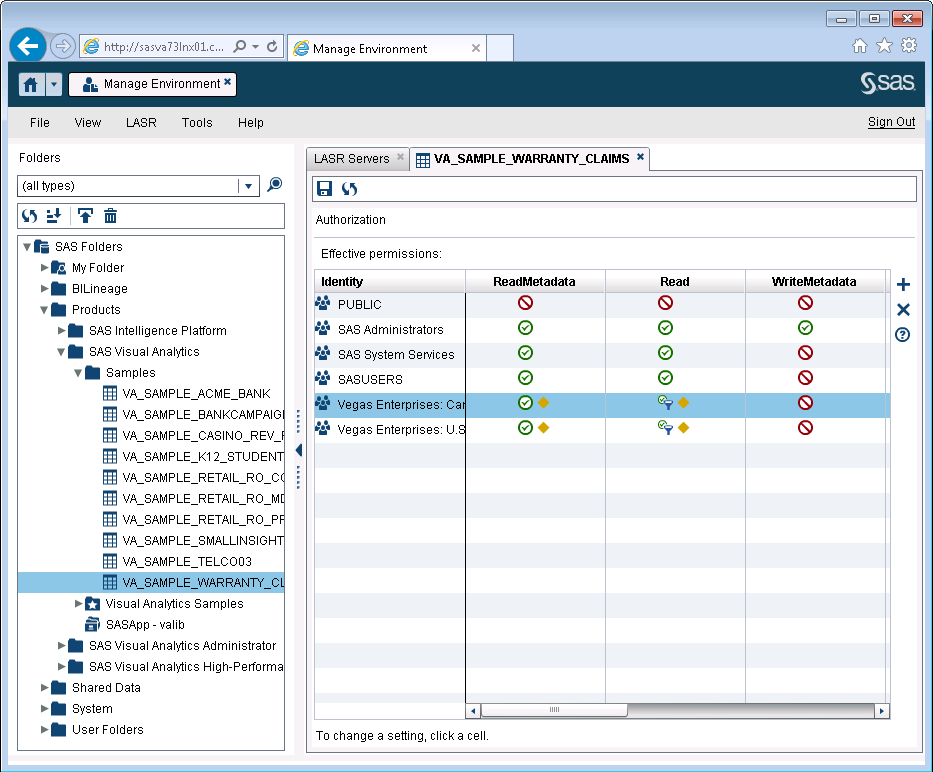
To illustrate here’s a screenshot of the Authorization tab in SAS Visual Analytics Administrator for a table that has 2 conditional grants applied – one each for the Canada and USA groups:
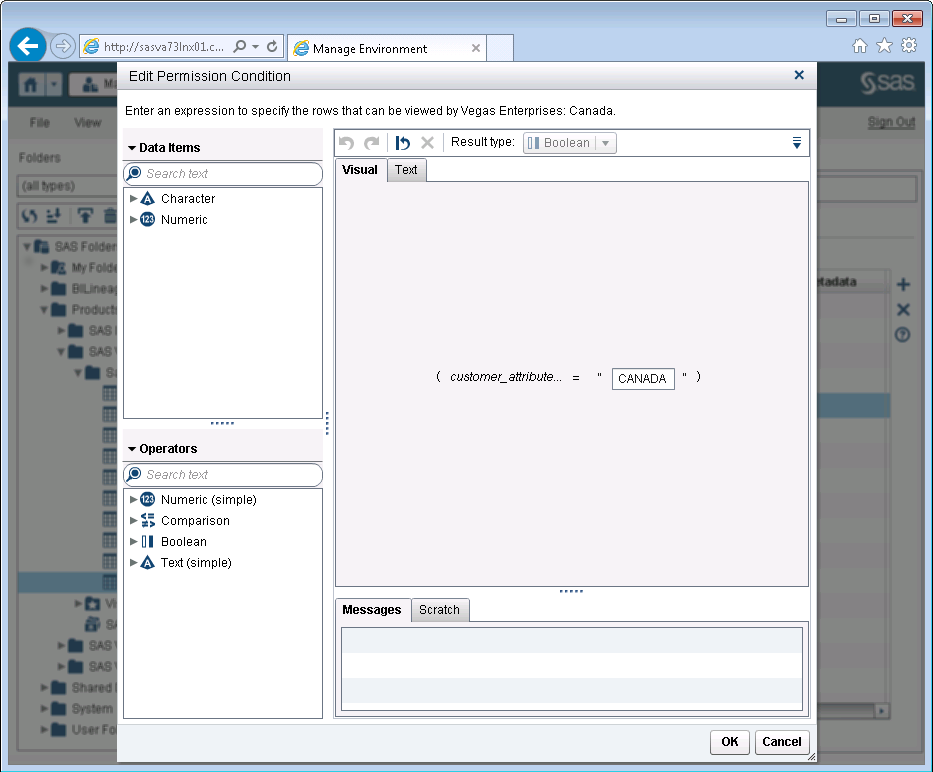
Looking at the Permission Condition for the Canada group we can see that members of that group are limited to rows where the customer_attribute_1 column has the value “CANADA”:
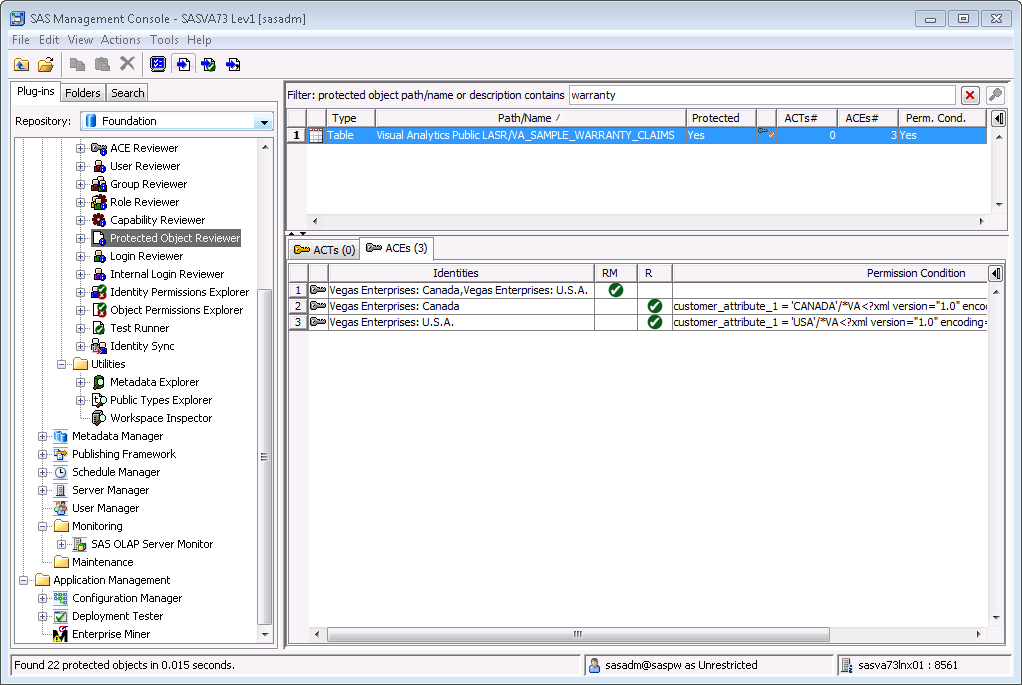
We can also see those permission conditions in the Metacoda Plug-ins Protected Object Reviewer:
Exporting Metadata Security Test XML from the Protected Object Reviewer in Metacoda Plug-ins 5.0 will now export additional tests to check those permission conditions. If we look at the exported test XML it looks something like this:
<SecTest ... >
<Objects>
<Object name="VA_SAMPLE_WARRANTY_CLAIMS" publicType="Table" parentFolder="Visual Analytics Public LASR">
<AccessControls complete="true">
<Group name="Vegas_CA" permissions="+RM,+R" condition="customer_attribute_1 = 'CANADA' ... " />
<Group name="Vegas_US" permissions="+RM,+R" condition="customer_attribute_1 = 'USA' ... />
</AccessControls>
</Object>
</Objects>
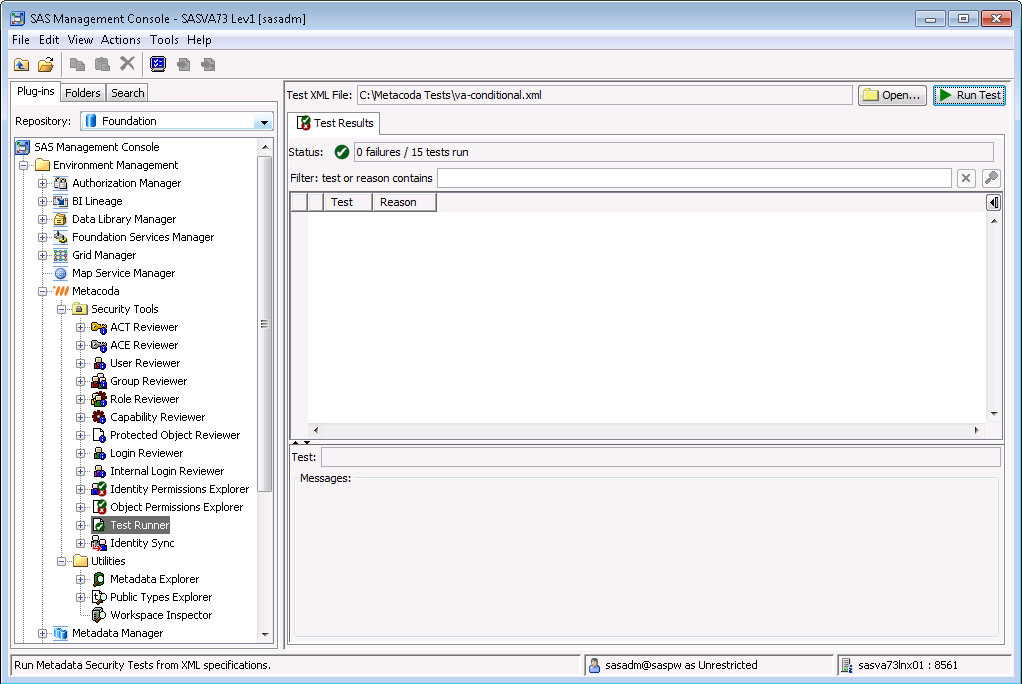
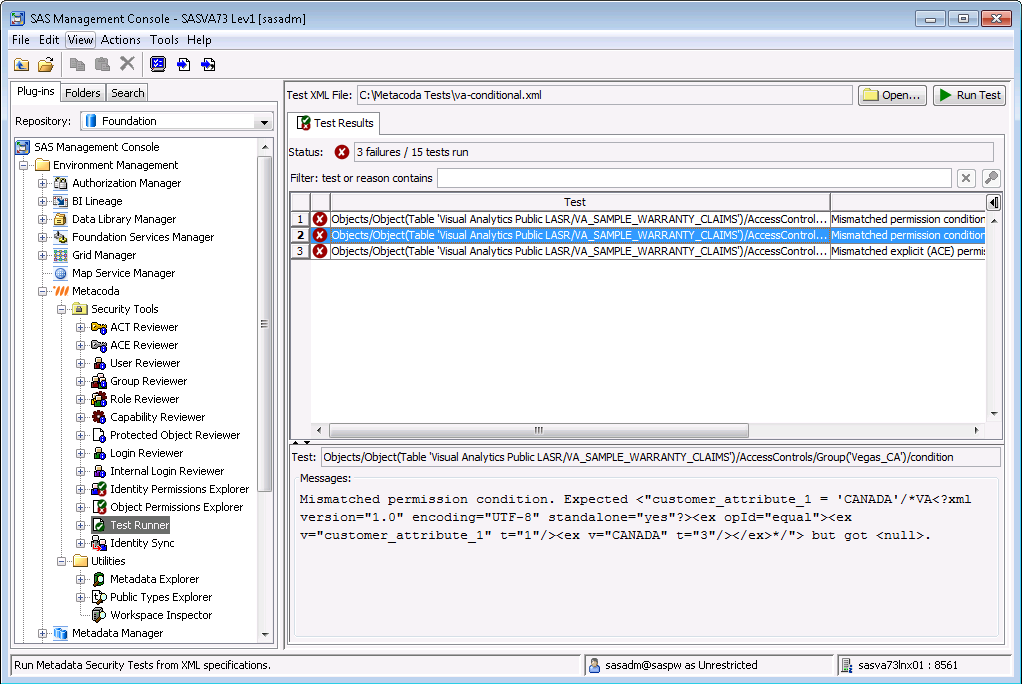
</SecTest>If we immediately run those tests interactively in the Metacoda Plug-ins Test Runner they should pass (the conditional grants haven’t been modified yet):
Then at some point in the future our regular scheduled batch testing might alert us to the fact that some tests are failing. If we run the conditional grant tests in the Test Runner plug-in again we might see the tests failing because someone has accidentally removed the conditional grant we expect to be in place for Canada:
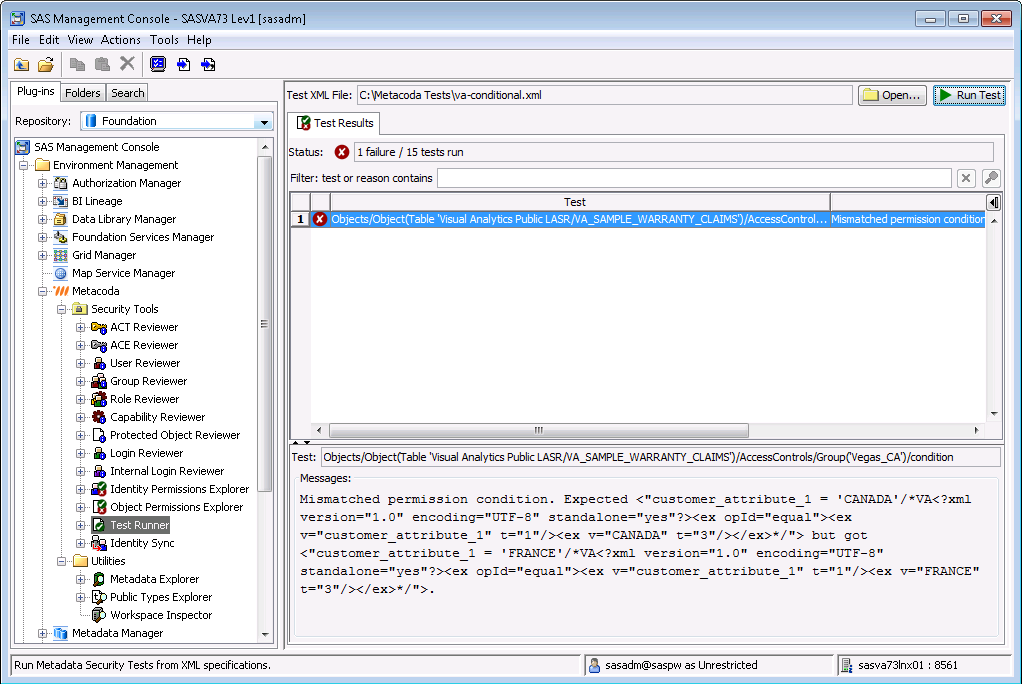
… or perhaps when they were adding a new conditional grant for France they accidentally modified the conditional grant for the Canada group and changed the country name from “CANADA” to “FRANCE”:
I hope this has shown you how the new permission condition tests in Metacoda Plug-ins 5.0 can help ensure row-level security access controls are correctly maintained for tables in SAS Visual Analytics. If you’d like to find out more about our metadata security testing framework, these new tests, or any of our other Metacoda Plug-ins, please contact me, or visit the metacoda.com web site.

Excellent as usual Paul, impressive.
Thanks Rafi!
Excellent stuff as usual Paul.
Using all the new stuff in anger at your latest client site in Western Australia and saving a lot of time while allowing the administrators to better understand the impact of actions taken.
:)
Thanks again.
Thanks Bob! That’s great to hear. Please let me know if you have any questions.
Hello Paul, Thank you for this topic. I’m facing a issue with SAS VA conditional grants. I’m ussing SAS VA 7.4 and I’m aiming to filter data by sas userid.
I tried in SAS VA administrator and in batch tool but it doesn’t work.
Here is my code in batch tools:
sas-set-metadata-access -host XXX -port XXX -user XXX -password “XXX” “/Shared Data/SAS Visual Analytics/Public/LASR/Toto(Table)” -grant sasusers:Read -condition “Parent_UserIdSAS=’SUB::SAS.Userid'”
In SAS VA administrator, I put the following conditions:
Parent_UserIdSAS=’SUB::SAS.Userid’
I tried with userid and userid@domain in capital letter, trim left, etc… but I think in my condition, It is impossible to find the macro variable.
Could you help me? Thanks a lot.
You condition looks ok to me. As long as your Parent_UserIdSAS values are uppercase to match the USERID or USERID@DOMAIN format that will be substituted I can’t see why it shouldn’t work. Have you tried manually applying a Parent_UserIdSAS=”MYUSERID” or Parent_UserIdSAS=”MYUSERID@MYDOMAIN” filter in VA to see if you get any rows returned? When you say it doesn’t work what happens? Do you see all unfiltered rows or no rows? Do you have any other explicit +R grants on the same table to any other users or groups (that the users might be members of)? SASUSERS is low-down in the identity hierarchy so any others (except for PUBLIC) would be above it and take precedence.
You may also want to ask SAS Tech Support on where you can see debug/troubleshooting logging of the filter that has been applied (after substitution of SUB::SAS.Userid). It’s been a while since I last did this so I can’t remember if that info was available. If I get some time to have a look after SAS Global Forum I’ll report back here.
Paul,
I need to open a report as if I’m ‘another person’, in order to test the Row Level Security. That is, I want to
pretend I’m John Smith, CFO, or Bob Smith, CIO, etc.
What is the simplest method, short of having the users actual logon info, to accomplish this.
Thanks.
Hi Gerry,
Ordinarily I would recommend using our Metacoda Object and Identity Permissions Explorer plug-ins to answer “who has access to this” and “what does this person have access to” type questions, but in this instance where you are trying to test row-level security, you could either work with the user to verify it, or look into user impersonation. Given sufficient privileges, as a SAS admin, it is possible to add another user id to a SAS identity and use it to log in and impersonate that user (there are limitations). There is a longer description of this in the following SAS Communities post:
https://communities.sas.com/t5/Administration-and-Deployment/How-can-I-impersonate-another-user/td-p/19563
I hope you find this useful.
Cheers
Paul
Hi Paul,
I have a table on which I have used a conditional grant by -condition “column1 in (‘USA’)”. But I want to disable/remove this grant and I wanted to view all the rows in the table back. I used -remove option in sas-ser-metadata-access but I can see the previous granted permission and unable to view all records back. Can you please help me on this?
Thanks in Advance for taking time to read my question! :-)
Hi,
You didn’t post the full command you used to remove the permission condition so I can’t comment on that. Assuming that it worked without error, then I would expect you to be able to see it has been removed when looking at the Authorization tab in SAS Management Console. If you can see it removed in SAS Management Console but it is still applied in another application then I understand some applications cache access controls so you may also want to try logout/login or restart. If the command had no errors, the condition is visibly removed when seen in SAS MC, but the condition is still applied, then your best option is to contact SAS Technical Support for further assistance.
Best of luck.
Paul