The SAS® METALIB Procedure, available in SAS 9.3, 9.2 and 9.1, is used to keep logical table metadata in sync with the physical tables that the metadata describes. It can also be used to report on any differences or discrepancies between the physical table and logical metadata descriptions. This post shows how ODS OUTPUT can be used in combination with PROC METALIB to capture its report output as SAS tables for further analysis and processing. Continue reading “SAS PROC METALIB and ODS OUTPUT”
Tag: SAS 9.1
Getting Certified

As a (certified) SAS platform administrator I often get asked how best to prepare for the SAS Certified Platform Administrator 9 exam.
I don’t have a magic formula other than study and experience. My standard response is to direct people to the best place I know where you can find out more: that’s the SAS support page specifically about exam preparation.
From my own experience I’d recommend the following steps:
Password Encoding with SAS
Quick note from Paul: I’m really excited that platformadmin.com’s very first guest post is from the well known blogger and author Tricia Aanderud. I suspect you already know Tricia, but just in case you don’t …
Tricia Aanderud, president of And Data, Inc., provides SAS® consulting services to corporations who need assistance understanding how to transform their data into meaningful charts, reports, and dashboards. Tricia has been an enthusiastic SAS user since 2002 and has presented papers at the SAS Global Forum and other industry conferences. She is the co-author of two SAS BI books, “Building Business Intelligence with SAS: Content Development Examples” and “The 50 Keys to Learning SAS Stored Processes”.
Now over to Tricia …
I frequently find myself querying the metadata to assist with understanding a new customer system or trying to navigate one of my demo systems. As a result, I find I have many utilities that I want to share with customers. However, since these connect to the metadata with an active password, I don’t want to share my password. Using the SAS PWENCODE procedure, I can encode my password in a SAS program and voilà! a way to share the code and shield the password.
Encoding the Password
The PWENCODE procedure allows you to encode passwords that are used in place of plaintext passwords in SAS programs.
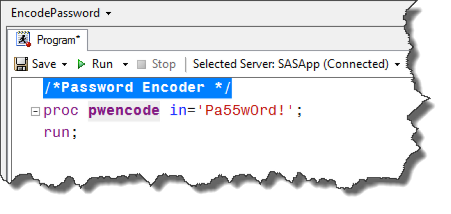
The following figure shows the PWENCODE procedure in a simple way. My example password, Pa55w0rd!, is placed in quotes. You can use different encoding methods, which you can read more about in the SAS PWENCODE procedure documentation.
The encoded password appears in the Continue reading “Password Encoding with SAS”
SAS Management Console over SSH
I was asked recently how to get SAS® Management Console to remotely access a SAS metadata server using SSH tunnels. In the absence of a VPN connection to your network, SSH can be an alternative for SAS Management Console access to a remote SAS metadata server.
I am a huge fan of SSH (Secure Shell). I have been using it several times a day for many years now. It’s great. If you haven’t heard of SSH before, take a look at the Wikipedia page for Secure Shell. Here’s a quote from the page that provides a nice intro/summary:
Secure Shell (SSH) is a network protocol for secure data communication, remote shell services or command execution and other secure network services between two networked computers that it connects via a secure channel over an insecure network.
Here are a couple of methods for using SAS Management Console over SSH:
1. Remote execution of SAS Management Console with X11 forwarding to the client
This method can be used when you are accessing a SAS platform installation on Linux or UNIX and have SSH client software and X server software on your remote workstation. Mac or Linux workstations are great for this since they usually have all the required software pre-installed. Windows can also be used if you obtain SSH client and X server software. I personally use Putty as an SSH client when I am working on Windows and would defintely recommend it. I have no specific recommendations for an X server on Windows since it’s been a long time since I’ve done X on Windows.
Assuming, as a SAS platform administrator, you have remote SSH access to the SAS metadata server machine then you can use SSH from your workstation to execute the SAS Management Console remotely and forward the X display to your client workstation.
Here’s an example command to do this:
ssh -X sasmeta.example.com /opt/sas93/SASManagementConsole/9.3/sasmc
Which means SSH connect, with X11 forwarding, to the machine sasmeta.example.com and then execute the SAS Management Console (/opt/sas93/SASManagementConsole/9.3/sasmc) on that remote machine sending the X windows back to the client workstation.
2. Local execution of SAS Management Console with SSH tunneling
SSH also allows you to configure a tunnel – a local port on your workstation that that forwards traffic to a designated server and port in the remote network. This tunnel can be used to make a remote service appear to be a local service. We can use it to make a remote SAS metadata server port appear to be on the local workstation so that a local installation of the SAS Management Console can connect to it as if it had a local metadata server.
Here’s an example command to do this:
ssh -L 8561:sasmeta.example.com:8561 sasmid.example.com
Which means SSH connect to the machine sasmid.example.com and establish a local machine port (8561) that forwards traffic to the remote host/port sasmeta.example.com:8561 accessible via sasmid.example.com. If you are not using public key authentication (recommended) then you will be prompted for a user id and password for the server. Once the connection is active, a local SAS Management Console can be started and will be able to access the remote SAS metadata server using a connection profile that connects to a metadata server on host/port localhost:8561. All traffic to this local port will be sent to the remote metadata server over the SSH tunnel.
Bear in mind that this only makes the metadata server port available on the local machine. So the local SAS Management Console instance can only access the metadata server. It doesn’t necessarily make the client fully functional as it may require additional connections to additional servers e.g. access to a SAS Object Spawner for a SAS Workspace Server session or a connection to the SAS Content Server. You could look into forwarding other ports and will also need to modify your local hosts file to redirect the remote host names found in metadata to the localhost interface. For anything more complex than pure metadata server access it would probably be easier and more robust to use a VPN connection (or remote access via something like X or RDP to remote network client workstations).
Metacoda Security Plug-ins Tip: Where’s that login?
This is a tip for Metacoda Security Plug-ins users who might have a need to track down which user or group identity in their SAS® metadata owns a particular user id.
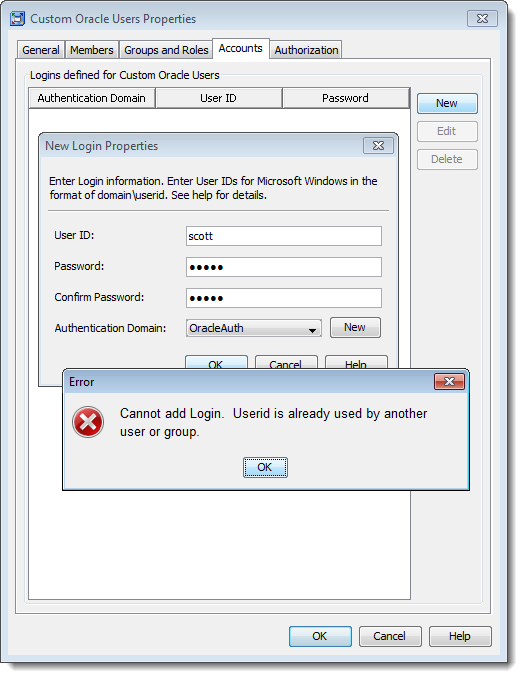
Have you ever gone to add a login to a user or group identity in the SAS Management Console, perhaps some database credentials for a group to share, but couldn’t because the userid had already been used elsewhere? If so then you’ll be familiar with this error:
So now you know the userid has already been used elsewhere, but where exactly? Maybe it shouldn’t have been used on the other identity, or maybe you just want to check out the other identity because you might be able to take advantage of it instead of adding a new one?
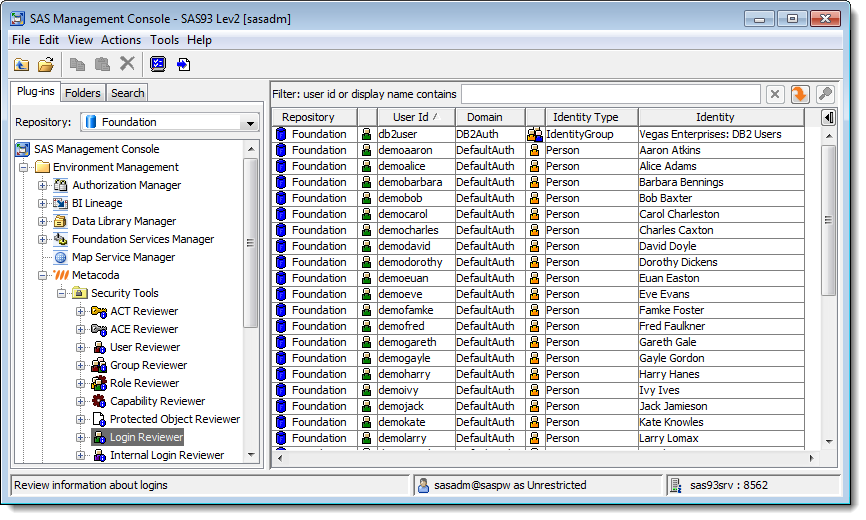
It’s easy to find that user id, and the user or group identity it is associated with, by using the Metacoda Security Plug-ins Login Reviewer, especially if you have the new 2.0 version (which works with SAS 9.3 and SAS 9.2).
To track down the login open the Login Reviewer:
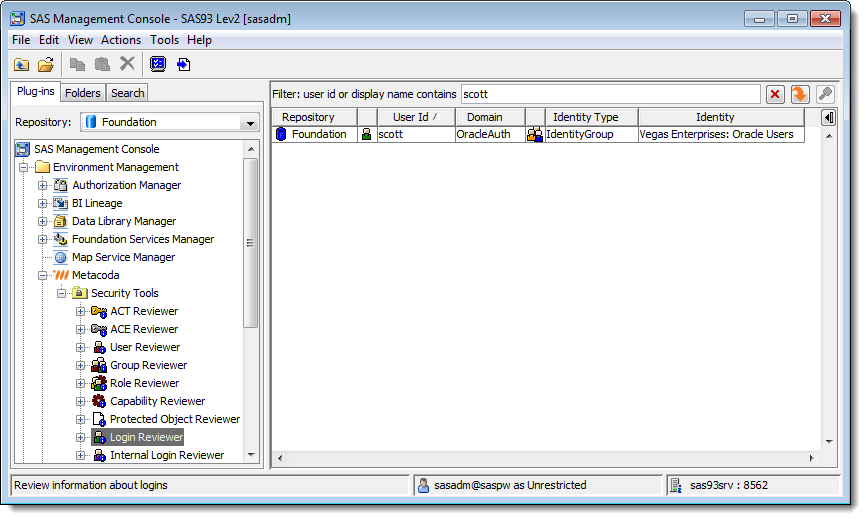
… and then, in the new filter bar, type in the user id which was already used, scott in this example. You’ll then see which identity has that login. In this example the scott login is already being used on the Vegas Enterprises: Oracle Users group which is why it couldn’t be added to the Custom Oracle Users group earlier.
If you have SAS 9.1.3 SP4 and Metacoda Security Plug-ins V1.0 then you won’t have the filter bar, but you can still find the login by clicking on the userid column header to sort by user id and then scroll down to find the problem login.
So finding a login isn’t that hard after all…