In my previous post on Finding Interesting SAS 9 Loggers, I highlighted 3 loggers I find useful for SAS 9 metadata access control change auditing, especially when using the new Metacoda Plug-ins 6.2 Activity Reviewer. There is also a 4th logger where you might already have trace level logging enabled, as it is configured so when you set up the SAS Environment Manager Service Architecture Audit, Performance, and Measurement (APM) component. In this post I want to go into more detail on each of those 4 loggers and explain what information they log and why I find them useful.
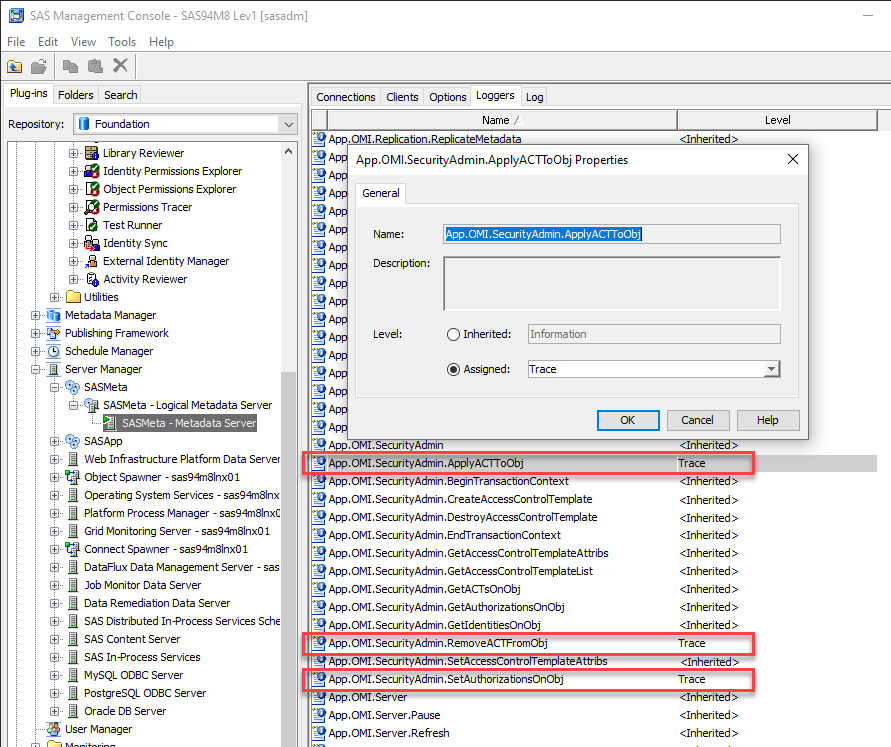
The loggers in question are:
- Audit.Meta.Security.AccCtrlAdm
- App.OMI.SecurityAdmin.SetAuthorizationsOnObj
- App.OMI.SecurityAdmin.ApplyACTToObj
- App.OMI.SecurityAdmin.RemoveACTFromObj
They all become interesting when they have a logging level of Trace and you are making changes to SAS9 metadata access controls, both Access Control Templates (ACTs) and Access Control Entries (ACEs, also known as explicit permissions). In the previous blog post I showed how you could temporarily enable Trace level logging for them using the SAS Management Console Server Manager plug-in Loggers tab. If you want to make this permanent then you can add the XML fragment below into the SAS Metadata Servers logging configuration file (e.g. /opt/sas94m8/config/Lev1/SASMeta/MetadataServer/logconfig.xml). The default configuration for the SAS Metadata Server, in the sasv9.cfg file, uses the logconfigloc system option to direct it to use the logging configuration in the logconfig.xml file. However, it is possible that post-installation configuration changes, such as when the SAS Environment Manager APM component is enabled, may have changed this setting to use a different logging config file. Check your sasv9*.cfg files in the MetadataServer directory and review the logconfigloc system option to confirm which log config file is in use.
<logger name="Audit.Meta.Security.AccCtrlAdm">
<level value="trace"/>
</logger>
<logger name="App.OMI.SecurityAdmin.ApplyACTToObj">
<level value="trace"/>
</logger>
<logger name="App.OMI.SecurityAdmin.RemoveACTFromObj">
<level value="trace"/>
</logger>
<logger name="App.OMI.SecurityAdmin.SetAuthorizationsOnObj">
<level value="trace"/>
</logger>
For more information about logging configuration see the SAS 9.4 Intelligence Platform: System Administration Guide and the Administering Logging for SAS Servers section.
Any changes you make to the logging configuration will take effect the next time the SAS Metadata Server is restarted (or earlier if you use proc iomoperate).
Now to look at some examples. In all of the following examples, the logging config as been modified to add (%c) so we can see which logger generated each line. There is more info on making this customization in a previous post Which logger did that SAS log message come from?
Add ACE to Metadata Folder
Ordinarily, when the sasadm@saspw user adds an ACE (PUBLIC:+RM) to the metadata folder /Test the Metadata Server log just has:
2023-09-29T15:03:48,444 INFO [00005286] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Access Control change on ObjectType=Tree, Name=Test, ObjId=A5TBCWBY.AA0001R5.
2023-09-29T15:03:48,460 INFO [00005293] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
You know an access control change was made to the folder, but little else.
When you have SAS Environment Manager APM configured, with its trace level logging for Audit.Meta.Security.AccCtrlAdm, then you will get more useful info:
2023-09-29T15:03:48,444 INFO [00005286] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Access Control change on ObjectType=Tree, Name=Test, ObjId=A5TBCWBY.AA0001R5.
2023-09-29T15:03:48,448 TRACE [00005286] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Trace log showing effective permissions protecting object: OMSOBJ:Tree/A5TBCWBY.AA0001R5.
SASAdministrators IdentityGroup Administer=AG|NG, CheckInMetadata=AG|ND, Delete=ND, Read=ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=AG|ND, WriteMemberMetadata=NG, Create=ND
SAS System Services IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
Vegas_AU_ACT IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=AG|ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
VegasExecs IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=AG|ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
PUBLIC IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=EG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
SASUSERS IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
2023-09-29T15:03:48,460 INFO [00005293] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
You can now see the trace logging from the Audit.Meta.Security.AccCtrlAdm logger where it shows effective permissions resulting from the changes. However, without a comparison to a previous state, you do not know how the access controls have been changed.
I like to add trace logging on App.OMI.SecurityAdmin.SetAuthorizationsOnObj as it gives you more detail on what was being changed:
2023-09-29T15:03:23,053 TRACE [00005282] (App.OMI.SecurityAdmin.SetAuthorizationsOnObj) 4:sasadm@saspw - IOM CALL {compRef:7f86e8057ce0}->OMI::SetAuthorizationsOnObj():
TransContext=0000000000000012
resource_spec=OMSOBJ:Tree/A5TBCWBY.AA0001R5
flags=0
authorizations=[0..0,0..4]
[0,0]=IdentityGroup
[0,1]=PUBLIC
[0,2]=G
[0,3]=ReadMetadata
[0,4]=
2023-09-29T15:03:23,053 TRACE [00005282] (App.OMI.SecurityAdmin.SetAuthorizationsOnObj) 4:sasadm@saspw - IOM RETURN 0={compRef:7f86e8057ce0}->OMI::SetAuthorizationsOnObj():
2023-09-29T15:03:48,444 INFO [00005286] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Access Control change on ObjectType=Tree, Name=Test, ObjId=A5TBCWBY.AA0001R5.
2023-09-29T15:03:48,448 TRACE [00005286] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Trace log showing effective permissions protecting object: OMSOBJ:Tree/A5TBCWBY.AA0001R5.
SASAdministrators IdentityGroup Administer=AG|NG, CheckInMetadata=AG|ND, Delete=ND, Read=ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=AG|ND, WriteMemberMetadata=NG, Create=ND
SAS System Services IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
Vegas_AU_ACT IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=AG|ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
VegasExecs IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=AG|ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
PUBLIC IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=EG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
SASUSERS IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
2023-09-29T15:03:48,460 INFO [00005293] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
In this case a Grant (G) on ReadMetadata to PUBLIC. You do need to be aware of timing with this, as the App.OMI.SecurityAdmin.SetAuthorizationsOnObj IOM CALL line happens after ticking the permission box in the Authorization tab, but it is possible that those changes may not have been saved (they could have been cancelled). In all likelihood the changes were saved because of what the subsequent Audit.Meta.Security.AccCtrlAdm lines show. Combining them all together gives a more complete picture of what happened, but you do need to be aware the App.OMI.SecurityAdmin.SetAuthorizationsOnObj lines are unsaved changes at the time they are logged.
For more info on SetAuthorizationsOnObj see the SAS Open Metadata Interface: Reference and Usage: SetAuthorizationsOnObj page which provides the meanings for the SetAuthorizationsOnObj parameters i.e.
- [0,2]=G means Grant
- [0,2]=D means Deny
- [0,2]=R means Remove
Remove ACE from Metadata Folder
This is me removing the same ACE I added above:
2023-09-29T15:15:59,935 TRACE [00005382] (App.OMI.SecurityAdmin.SetAuthorizationsOnObj) 4:sasadm@saspw - IOM CALL {compRef:7f86e8057ce0}->OMI::SetAuthorizationsOnObj():
TransContext=0000000000000013
resource_spec=OMSOBJ:Tree/A5TBCWBY.AA0001R5
flags=0
authorizations=[0..0,0..4]
[0,0]=IdentityGroup
[0,1]=PUBLIC
[0,2]=R
[0,3]=ReadMetadata
[0,4]=
2023-09-29T15:15:59,936 TRACE [00005382] (App.OMI.SecurityAdmin.SetAuthorizationsOnObj) 4:sasadm@saspw - IOM RETURN 0={compRef:7f86e8057ce0}->OMI::SetAuthorizationsOnObj():
2023-09-29T15:16:03,026 INFO [00005387] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Access Control change on ObjectType=Tree, Name=Test, ObjId=A5TBCWBY.AA0001R5.
2023-09-29T15:16:03,029 TRACE [00005387] (Audit.Meta.Security.AccCtrlAdm) 4:sasadm@saspw - Trace log showing effective permissions protecting object: OMSOBJ:Tree/A5TBCWBY.AA0001R5.
SASAdministrators IdentityGroup Administer=AG|NG, CheckInMetadata=AG|ND, Delete=ND, Read=ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=AG|ND, WriteMemberMetadata=NG, Create=ND
SAS System Services IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
Vegas_AU_ACT IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=AG|ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
VegasExecs IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=AG|ND, ReadMetadata=AG|NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
PUBLIC IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=ND, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
SASUSERS IdentityGroup Administer=ND, CheckInMetadata=ND, Delete=ND, Read=ND, ReadMetadata=NG, Write=ND, WriteMetadata=ND, WriteMemberMetadata=ND, Create=ND
2023-09-29T15:16:03,042 INFO [00005394] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
Add ACT to Metadata Folder
These loggers become even more useful with ACTs. Without the addition of the trace level loggers discussed in this post, when the sasadm@saspw user applies an ACT to the metadata folder /Test the Metadata Server log would ordinarily only log the following:
2023-09-29T15:31:01,763 INFO [00004855] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
This tells you the folder was modified but there is no indication of any access control change. This is also the case with SAS Environment Manager APM configured, as the Audit.Meta.Security.AccCtrlAdm logger does not seem to log anything about applying or removing ACTs from objects.
However, by turning on trace level logging with the App.OMI.SecurityAdmin.ApplyACTToObj you can get more information:
2023-09-29T15:34:58,760 TRACE [00004837] (App.OMI.SecurityAdmin.ApplyACTToObj) 4:sasadm@saspw - IOM CALL {compRef:7f86e8057ce0}->OMI::ApplyACTToObj():
TransContext=0000000000000011
resource_spec=OMSOBJ:Tree/A5TBCWBY.AA0001R5
flags=0
ACTresource_spec=OMSOBJ:AccessControlTemplate/A5TBCWBY.AO000008
2023-09-29T15:34:58,761 TRACE [00004837] (App.OMI.SecurityAdmin.ApplyACTToObj) 4:sasadm@saspw - IOM RETURN 0={compRef:7f86e8057ce0}->OMI::ApplyACTToObj():
2023-09-29T15:35:01,759 INFO [00004850] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
This indicates that the sasadm user applied an ACT with id A5TBCWBY.AO000008 to a metadata folder (Tree object) with id A5TBCWBY.AA0001R5. Whilst it is not readily apparent which ACT and which folder, these can both be looked up by their id values. When using the Metacoda Activity Reviewer plug-in to view the related log lines, you can right mouse and select Advanced Properties to open a dialog with information about the objects.
As with the App.OMI.SecurityAdmin.SetAuthorizationsOnObj logger, the App.OMI.SecurityAdmin.ApplyACTToObj IOM CALL line gets logged after closing the ACTs dialog, but before the changes are saved to the object, so once again it is possible the changes could have been cancelled. However, the subsequent Audit Public Object lines do suggest the ACT changes were likely saved, but is not guaranteed. If you do want to be sure about changes relating the the application or removal of ACTs on objects, I would of course recommend using the Metacoda Security Testing Framework as it can be scheduled to check that the current definition and application of ACTs matches the before-state represented when the tests it runs were exported. For example you could batch export overnight and run the tests the following night. Any test failures will be ACT changes remaining after that 24 hour period. The logs can then be used to trace when the changes were made and by whom.
For more info on ApplyACTToObj see the SAS Open Metadata Interface: Reference and Usage: ApplyACTToObj page.
Remove ACT from Metadata Folder
This is me removing the same ACT I added above:
2023-09-29T15:38:36,865 TRACE [00004701] (App.OMI.SecurityAdmin.RemoveACTFromObj) 4:sasadm@saspw - IOM CALL {compRef:7f86e8057ce0}->OMI::RemoveACTFromObj():
TransContext=0000000000000010
resource_spec=OMSOBJ:Tree/A5TBCWBY.AA0001R5
flags=0
ACTresource_spec=OMSOBJ:AccessControlTemplate/A5TBCWBY.AO000005
2023-09-29T15:38:36,866 TRACE [00004701] (App.OMI.SecurityAdmin.RemoveACTFromObj) 4:sasadm@saspw - IOM RETURN 0={compRef:7f86e8057ce0}->OMI::RemoveACTFromObj():
2023-09-29T15:38:39,240 INFO [00004714] (Audit.Meta.Updates.PublicObjects) 4:sasadm@saspw - Audit Public Object Type=Folder Name=Test ObjId=A5TBCWBY.AA0001R5 has been updated.
In this case it is a different logger, App.OMI.SecurityAdmin.RemoveACTFromObj, that is logging the as-yet-unsaved removal of the ACT from the object followed by Audit.Meta.Updates.PublicObjects lines that show the object was modified.
For more info on RemoveACTFromObj see the SAS Open Metadata Interface: Reference and Usage: ApplyACTToObj page.
I hope you found this post useful for tracing access control changes in SAS metadata. Please post any comments about any other SAS 9 loggers you have found interesting or useful in your work.
